While specific encryption methods for AI glasses have not been universally defined, several established techniques are likely to be employed to enhance data security and privacy. Here are some commonly used encryption methods that could be relevant:
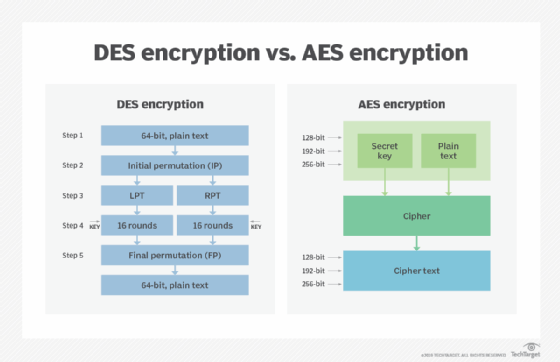
1. AES (Advanced Encryption Standard)
- Description: A symmetric encryption algorithm widely used for securing data.
- Application: It can be used for encrypting stored data on the device and for secure communication between the glasses and other devices.
2. RSA (Rivest-Shamir-Adleman)
- Description: An asymmetric encryption algorithm that uses a pair of keys (public and private) for secure data transmission.
- Application: Useful for securely exchanging keys between devices or for signing data.
3. TLS (Transport Layer Security)
- Description: A protocol that provides secure communication over a computer network.
- Application: Ensures that data transmitted between the AI glasses and cloud services or other devices is encrypted and secure from eavesdropping.
4. ECC (Elliptic Curve Cryptography)
- Description: A form of public key cryptography that offers similar security to RSA but with smaller key sizes, making it efficient for devices with limited processing power.
- Application: Suitable for establishing secure connections and authentication processes in AI glasses.
5. Hashing Algorithms (e.g., SHA-256)
- Description: Used to create a fixed-size hash value from input data, ensuring data integrity.
- Application: This can be used to verify the integrity of data being transmitted or stored, ensuring it hasn’t been altered.
6. End-to-End Encryption (E2EE)
- Description: A method of data transmission where only the communicating users can read the messages.
- Application: Ensures that data sent from the AI glasses to another party is only accessible to the intended recipient.
7. Secure Multi-Party Computation
- Description: A technique that allows multiple parties to compute a function over their inputs while keeping those inputs private.
- Application: Useful for collaborative applications where privacy is essential.
8. Homomorphic Encryption
- Description: Allows computations to be performed on encrypted data without needing to decrypt it first.
- Application: Could be useful for processing data in the cloud while maintaining user privacy.
By implementing a combination of these encryption methods, AI glasses can enhance their data security framework, protecting user information from unauthorized access and ensuring privacy during data transmission and storage.


